In the ever-evolving landscape of cyber threats, a new player has emerged, demonstrating an alarming level of sophistication and effectiveness. Known as the Meduza Stealer, this malware is taking data theft to new levels, posing a significant threat to individuals and organizations.
What is Meduza Stealer?
Meduza Stealer is a potent piece of malware that has been designed with one primary goal: to steal sensitive information from infected systems. It is a type of infostealer, a category of malware that focuses on extracting valuable data, such as login credentials, financial information, and other personal details.
Even more concerning is its authors actively developing the malware to evade detection. This measure has seen some success and proven effective against many antivirus software. This ability to avoid detection increases the malware’s effectiveness and, by extension, its commercial value.
How Meduza Stealer Works
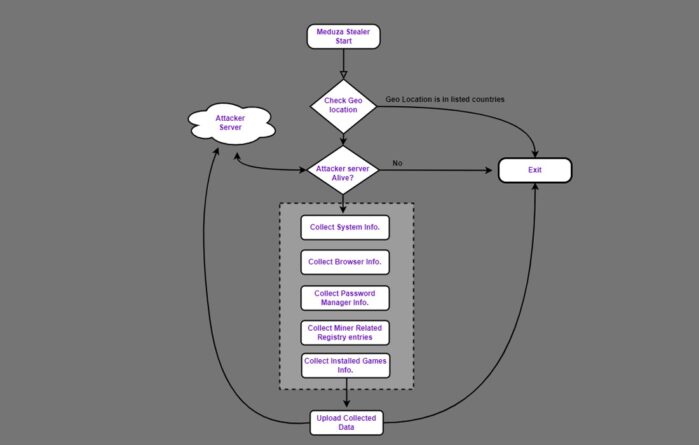
The Meduza Stealer operates stealthily and efficiently, making it a formidable threat. It begins by infiltrating the target system, often through phishing emails or malicious downloads. Once inside, it starts its data harvesting process.
The malware is capable of stealing a wide range of data, including but not limited to:
- Browser data: Meduza can extract saved passwords, autofill data, cookies, and history from popular browsers like Google Chrome, Mozilla Firefox, and Microsoft Edge.
- Cryptocurrency wallets: Meduza can steal data from cryptocurrency wallets, including Bitcoin, Ethereum, and Litecoin.
- FTP clients: The malware can extract credentials from popular FTP clients.
- Gaming software: Meduza can steal account information from gaming platforms like Steam.
- Messaging apps: Meduza can extract login credentials and chat history from messaging apps like Discord and Telegram.
One of the distinguishing features of Meduza Stealer is its ability to bypass User Account Control (UAC), a security feature in Windows. This allows the malware to execute its operations without triggering any alerts, making it even more dangerous.
Who Does Meduza Stealer Target or Ignore?
Meduza Stealer targets a broad audience but is specifically designed to avoid certain countries. If the malware scans for geolocation data and finds a match with any of the following countries, it aborts its operations:
- Russia
- Kazakhstan
- Belarus
- Georgia
- Turkmenistan
- Uzbekistan
- Armenia
- Kyrgyzstan
- Moldova
- Tajikistan
This strategic targeting and avoidance make Meduza Stealer a unique threat in the world of cybercrime. It’s important to note that the malware is under active development and is being marketed aggressively across various cybercrime forums and Telegram channels.
How Meduza Stagarzer is Being Monetized
The creators of Meduza Stealer have taken a unique approach to distributing and monetizing their malware, employing sophisticated marketing strategies to promote it.
One of the critical aspects of Meduza Stealer’s commercialization is its subscription-based model. The authors offer different subscription plans, including one-month, three-month, and lifetime access.
This sales model allows potential cyber criminals to access the malware and its capabilities for a fee, effectively turning cybercrime into a service. It’s an especially concerning trend in the world of cybercrime, allowing those with limited technical skills to launch sophisticated cyberattacks.
Meduza Stealer is a versatile tool and can target 19 password manager apps, 76 crypto wallets, the Steam gaming client, and the Discord messaging app. This broad targeting capability increases the potential value of the stolen data, making the malware more appealing to potential subscribers.
How Subscribers Access Stolen Data
Subscribers are given access to a management console to view and manage the data stolen by the malware. This includes a wide range of information, from system and browser info to password manager data and details about installed games.
How to Protect Yourself Against Meduza Stealer
Now that we understand the threat of Meduza Stealer let’s delve into some practical steps to protect ourselves and our organizations from this potent malware.
Regular Software Updates
One of the most effective ways to protect against malware like Meduza Stealer is by regularly updating all software. This includes your operating system, web browsers, and any applications you use. Software updates often include patches for security vulnerabilities that malware can exploit.
Use a Reliable Antivirus
Having reliable and updated antivirus software is a must. These tools can detect and remove a wide range of malware, including infostealers like Meduza. Ensure that your antivirus is set to update automatically and perform regular scans.
Be Wary of Phishing Attempts
As mentioned earlier, one of the common ways Meduza infiltrates systems is through phishing emails. Be cautious of any unexpected or suspicious emails, especially those containing links or attachments. Only provide your personal information if you’re sure the request is legitimate.
Secure Your Cryptocurrency Wallets
If you’re a cryptocurrency user, securing your wallet is crucial. Use hardware wallets like Trezor, generally more secure than software wallets. Also, consider using wallets that require multi-factor authentication.
Educate Yourself and Your Team
Knowledge is power, especially when it comes to cybersecurity. Stay informed about the latest threats and how to combat them. If you’re part of an organization, consider implementing regular cybersecurity training for all employees.
Understanding The Threat Landscape
The emergence of Meduza Stealer underscores the evolving nature of cyber threats. As malware becomes more sophisticated, the potential for damage increases exponentially. Meduza, with its wide range of data theft capabilities and stealthy operation, represents a significant threat.
Individuals and organizations must stay vigilant and adopt robust cybersecurity measures. This includes maintaining up-to-date antivirus software, practicing safe browsing habits, and educating users about the dangers of phishing emails and malicious downloads.
In the face of threats like Meduza Stealer, a proactive approach to cybersecurity is more important than ever. As the saying goes, “An ounce of prevention is worth a pound of cure.” In the realm of cybersecurity, this couldn’t be more accurate.


