The number of attacks using malicious mobile software nearly doubled over the course of 2018. Last year, there were 116.5 million attacks, compared to 66.4 million in 2017, with a significant increase in unique users being affected. Globally, Malaysia was ranked 11th, with 22.81% of users attacked by mobile malware.
Despite more devices being attacked, the number of malware files has decreased, leading researchers to conclude that the quality of mobile malware has become more impactful and precise. As the world becomes more mobile, the role of smartphones in business processes and day to day life is growing rapidly.
In response, cybercriminals are paying more attention to how they are distributing malware and the attack vectors used. The channels through which malware is delivered to users and infects their devices is a key part of the success of a malicious campaign today, taking advantage of those users who do not have any security solutions installed on their phones.
The success of the distribution strategies is demonstrated not only by the increase in attacks, but also the number of unique users that have encountered malware. In 2018 this figure rose by 774,000 on the previous year, to 9,895,774 affected users. Among the threats encountered, the most significant growth was in the use of Trojan-Droppers, whose share almost doubled from 8.63% to 17.21%. This type of malware is designed to bypass system protection and deliver there all sorts of malware, from banking Trojans to ransomware.
“In 2018, mobile device users faced what could have been the fiercest cybercriminal onslaught ever seen. Over the course of the year, we observed both new mobile device infection techniques, such as DNS hijacking, along with an increased focus on enhanced distribution schemes, like SMS spam. This trend demonstrates the growing need for mobile security solutions to be installed on smartphones – to protect users from device infection attempts, regardless of the source,” said Viсtor Chebyshev, security expert at Kaspersky Lab.
In 2018, Kaspersky Lab products and technologies detected:
- 5,321,142 malicious installation packages
- 151,359 new mobile banking Trojans
- 60,176 new mobile ransomware Trojans
Mobile Device Infection Trends in 2018
Users of mobile devices in 2018 faced what may have been the fiercest cybercriminal onslaught ever seen. Over the course of the year both new mobile device infection techniques (for example, DNS hijacking) and a step-up in the use of tried-and-tested distribution schemes (for example, SMS spam) were seen.
Virus writers focused on:
- Droppers (Trojan-Dropper), designed to bypass detection
- Attacks on bank accounts via mobile devices
- Apps that can be used by cybercriminals to cause damage (RiskTool)
- Adware apps
In 2018, Kaspersky Lab uncovered three mobile APT campaigns aimed primarily at spying on victims, including reading messages in social networks.
Banking Malware Profile Rises Significantly
Last year’s stats on the number of attacks involving mobile banking Trojans were eye-catching. At the beginning of 2018, it seemed that this type of threat had stabilized both by number of unique samples discovered and by number of users attacked. However, already by Q2 the situation had radically changed for the worse.
New records were set in terms of both number of mobile banking Trojans detected and number of attacked users. The root cause of this hike is not clear, but the main culprits are the creators of the Asacub and Hqwar Trojans. The former has quite a long history – according to Kaspersky Lab data, the group behind it has been at work for more than three years.
Asacub itself evolved from an SMS Trojan that was armed from the get-go with tools to counteract deletion and intercept incoming calls and SMS messages. Later, the creators of the malware beefed up its logic and began mass distribution using the same attack vector as before: social engineering via SMS. Online forums where people often expect messages from unfamiliar users became a source of mobile numbers. Next, the avalanche propagation method kicked in, with infected devices themselves becoming distributors – Asacub sent itself to everyone in the victim’s phone book.
However, banking Trojans in 2018 were noteworthy not just in terms of scale but mechanics as well. One aspect of this is the increasingly common use of Accessibility Services in banking threats. This is partly a response to new versions of Android that make it increasingly difficult to overlay phishing windows on top of banking apps, and partly the fact that using Accessibility allows the Trojan to lodge itself in the device so that users cannot remove it by themselves.
What’s more, cybercriminals can use Accessibility Services to hijack a perfectly legitimate application and force it, say, to launch a banking app to make a money transfer right there on the victim’s device. Techniques have also appeared to counter dynamic analysis; for example, the Rotexy Trojan checks to see if it is running in a sandbox.
That said, it should be noted that combined with obfuscation, anti-dynamic analysis techniques can be effective if virus writers manage to infiltrate their Trojan into a popular app store, in which case both static and dynamic processing may be powerless. Although sandbox detection cannot be said to be common practice among cybercriminals, the trend is evident, and Kaspersky believes that such techniques will become very sophisticated in the near future.
Top 10 countries by share of users attacked by mobile malware
| Country* | %** |
| Iran | 44.24 |
| Bangladesh | 42.98 |
| Nigeria | 37.72 |
| India | 36.08 |
| Algeria | 35.06 |
| Indonesia | 34.84 |
| Pakistan | 32.62 |
| Tanzania | 31.34 |
| Kenya | 29.72 |
| Philippines | 26.81 |
* Excluded from the rating are countries with fewer than 25,000 active users of Kaspersky Lab mobile solutions over the reporting period.
** Unique users attacked in the country as a percentage of all users of Kaspersky Lab mobile solutions in the country.
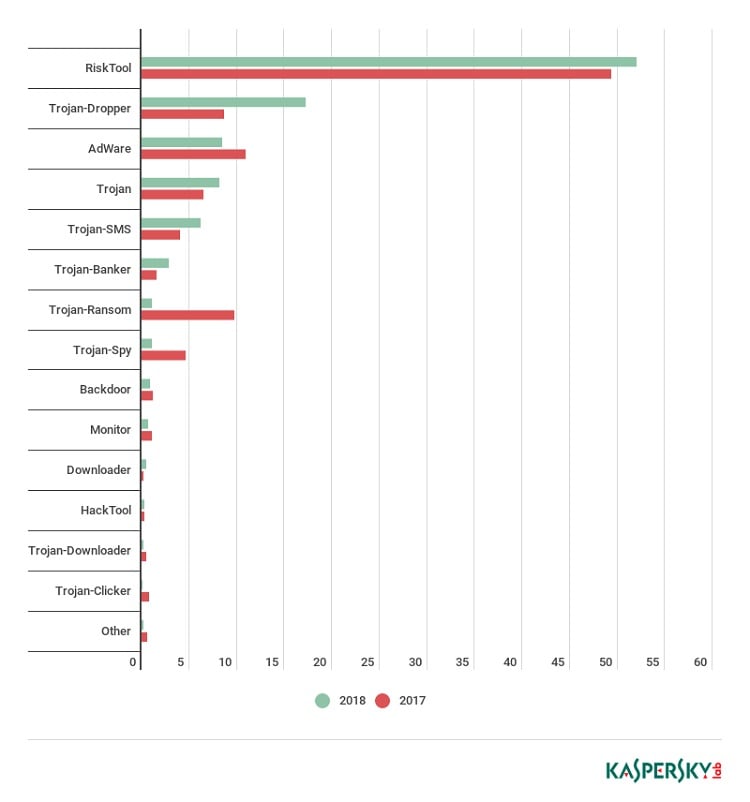
Types of Mobile Malware
Of all detected threats in 2018, the situation with mobile ransomware Trojans (1.12%) was the rosiest, with their share cut drastically by 8.67 p.p. It was a similar story with spyware Trojans (1.07%), whose share fell by 3.55 p.p. Adware apps (8.46%) also lost ground in comparison with 2017.
Trojan-Dropper threats were a marked exception, almost doubling their share from 8.63% to 17.21%. This growth reflects cybercriminals’ appetite to use mobile droppers to wrap all sorts of payloads: banking Trojans, ransomware, adware, etc. This trend looks set to continue in 2019.
Unfortunately, like Trojan-Dropper, the share of financial threats in the shape of mobile bankers also practically doubled – from 1.54% to 2.84%.
Surprisingly, SMS Trojans (6.20%) made the Top 5 in terms of number of objects detected. This dying breed of threats is common only in a handful of countries, but that did not stop its share from increasing against 2017. Although there is no imminent talk of a revival of this class, it is still worth disabling paid subscriptions on your mobile device.
Conclusion
For seven years now, the world of mobile threats has been constantly evolving, not only in terms of number of malicious programs and technological refinement of each new malware modification but also due to the increasing ways in which money and valuable information can be acquired using mobile devices. The year 2018 showed that a relative lull in certain types of malware can be followed by an epidemic. Last year, it was the banking Trojan Asacub and co.; in 2019 it could be a wave of ransomware, seeking to make up lost ground.